Setting up MikroTik RouterOS™
Description
Downloading and Installing the MikroTik RouterOS™ The download and installation process of the MikroTik RouterOS™ is described in the following diagram:
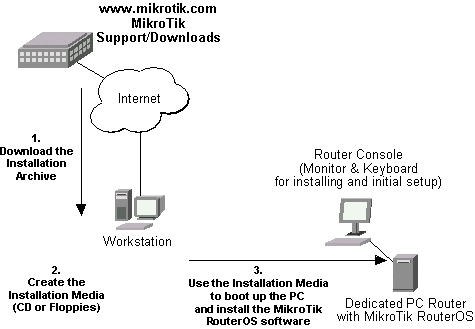
- Download the basic installation archieve file.
Depending on the desired media to be used for installing the MikroTik RouterOS™ please chose one of the following archive types for downloading:
- ISO image - of the installation CD, if you have a CD writer for creating CDs. The ISO image is in the MTcdimage_v2-9-x_dd-mmm-yyyy_(build_z).zip archive file containing a bootable CD image. The CD will be used for booting up the dedicated PC and installing the MikroTik RouterOS™ on its hard-drive or flash-drive.
- Netinstall - if you want to install RouterOS over a LAN with one floppy boot disk, or alternatively using PXE or EtherBoot option supported by some network interface cards, that allows truly networked installation. Netinstall program works on Windows 95/98/NT4/2K/XP.
- MikroTik Disk Maker - if you want to create 3.5" installation floppies. The Disk Maker is a self-extracting archive DiskMaker_v2-9-x_dd-mmm-yyyy_(build_z).exe file, which should be run on your Windows 95/98/NT4/2K/XP workstation to create the installation floppies. The installation floppies will be used for booting up the dedicated PC and installing the MikroTik RouterOS™ on its hard-drive or flash-drive.
- Create the installation media.
Use the appropriate installation archive to create the Installation CD or floppies.
- For the CD, write the ISO image onto a blank CD.
- For the floppies, run the Disk Maker on your Windows workstation to create the installation floppies. Follow the instructions and insert the floppies in your FDD as requested, label them as Disk 1,2,3, etc.
- Install the MikroTik RouterOS™ software.
Your dedicated PC router hardware should have:
- CPU and motherboard - advanced 4th generation (core frequency 100MHz or more), 5th generation (Intel Pentium, Cyrix 6X86, AMD K5 or comparable) or newer uniprocessor Intel IA-32 (i386) compatible (multiple processors are not supported)
- RAM - minimum 64 MiB, maximum 1 GiB; 64 MiB or more recommended
- Hard Drive/Flash - standard ATA interface controller and drive (SCSI and USB controllers and drives are not supported; RAID controllers that require additional drivers are not supported) with minimum of 64 Mb space
Hardware needed for installation time only
Depending on installation method chosen the router must have the following hardware:
- Floppy-based installation - standard AT floppy controller and 3.5'' disk drive connected as the first floppy disk drive (A); AT, PS/2 or USB keyboard; VGA-compatible video controller card and monitor
- CD-based installation - standard ATA/ATAPI interface controller and CD drive supporting "El Torito" bootable CDs (you might need also to check if the router's BIOS supports booting from this type of media; if El Torito is not supported by the BIOS, you can still boot up from the CD using Smart Boot Manager Floppy); AT, PS/2 or USB keyboard; VGA-compatible video controller card and monitor
- Floppy-based network installation - standard AT floppy controller and 3.5'' disk drive connected as the first floppy disk drive (A); PCI Ethernet network interface card supported by MikroTik RouterOS (see the Device Driver List for the list)
- Full network-based installation - PCI Ethernet network interface card supported by MikroTik RouterOS (see the Device Driver List for the list) with PXE or EtherBoot extension booting ROM (you might need also to check if the router's BIOS supports booting from network)
Note that if you use Netinstall, you can license the software during the installation procedure (the next point of this section describes how to do it).
Boot up your dedicated PC router from the Installation Media you created and follow the instructions on the console screen while the HDD is reformatted and MikroTik RouterOS installed on it. After successful installation please remove the installation media from your CD or floppy disk drive and hit 'Enter' to reboot the router.
- License the software.
When booted, the software allows you to use all its features for 24 hours (note that you can pause the countdown by shutting down the router). If the license key will not be entered during this period of time, the router will become unusable, and will need a complete reinstallation.
RouterOS licensing scheme is based on software IDs. To license the software, you must know the software ID. It is shown during installation procedures, and also you can get it from system console or Winbox. To get the software ID from system console, type: /system license print (note that you must first log in the router; by default there is user admin with no password (just press [Enter] key when prompted for password)). See sections below on basic configuration of your router
Once you have the ID, you can obtain a license:
Notes
The hard disk will be entirely reformatted during the installation and all data on it will be lost!
You can move the hard drive with MikroTik RouterOS installed to a new hardware without loosing a license, but you cannot move the RouterOS to a different hard drive without purchasing an another license (except hardware failure situations). For additional information write to key-support@mikrotik.com.
Note! Do not use MS-DOS format command or other disk format utilities to reinstall your MikroTik router! This will cause the Software-ID to change, so you will need to buy another license in order to get MikroTik RouterOS running.
Logging into the MikroTik Router
Description
Normally you connect to the router by IP addresses with any telnet or SSH client software (a simple text-mode telnet client is usually called telnet and is distributed together with almost any OS). You can also use graphical configuration tool for Windows (also can be run in Linux using Wine) called Winbox. To get Winbox, connect to the router's IP address with a web browser, and follow the link to download winbox.exe from the router.
MAC-telnet is used to connect to a router when there is no other way to connect to it remotely if the router has no IP address or in case of misconfigured firewall. MAC-telnet can only be used from the same broadcast domain (so there should be no routers in between) as any of the router's enabled interfaces (you can not connect to a disabled interface). MAC-telnet program is a part of the Neighbor Viewer. Download it from www.mikrotik.com, unpack both files contained in the archive to the same directory, and run NeighborViewer.exe. A list of MikroTik routers working in the same broadcast domain will be showed double-click the one you need to connect to. Note that Winbox is also able to connect to routers by their MAC addresses, and has the discovery tool built-in.
You can also connect to the router using a standard DB9 serial null-modem cable from any PC. Default settings of the router's serial port are 9600 bits/s (for RouterBOARD 500 series - 115200 bits/s), 8 data bits, 1 stop bit, no parity, hardware (RTS/CTS) flow control. Use terminal emulation program (like HyperTerminal or SecureCRT in Windows, or minicom in UNIX/Linux) to connect to the router. The router will beep twice when booted up, and you should see the login prompt shortly before that (check cabling and serial port settings if you do not see anything in the terminal window).
When logging into the router via terminal console, you will be presented with the MikroTik RouterOS™ login prompt. Use 'admin' and no password (hit [Enter]) for logging in the router for the first time, for example:
MikroTik v2.9
Login: admin
Password:
The password can be changed with the /password command.
[admin@MikroTik] > password
old password:
new password: ************
retype new password: ************
[admin@MikroTik] >
Adding Software Packages
Description
The basic installation comes only with the system package. This includes basic IP routing and router administration. To have additional features such as IP Telephony, OSPF, wireless and so on, you will need to download additional software packages.
The additional software packages should have the same version as the system package. If not, the package won't be installed. Please consult the MikroTik RouterOS™ Software Package Installation and Upgrading Manual for more detailed information about installing additional software packages.
To upgrade the router packages, simply upload the packages to the router via ftp, using the binary transfer mode. After you have uploaded the packages, reboot the router, and the features that are provided by those packages will be available (regarding your license type, of course).
Navigating The Terminal Console
Description
Welcome Screen and Command Prompt After logging into the router you will be presented with the MikroTik RouterOS™ Welcome Screen and command prompt, for example:
MMM MMM KKK TTTTTTTTTTT KKK
MMMM MMMM KKK TTTTTTTTTTT KKK
MMM MMMM MMM III KKK KKK RRRRRR OOOOOO TTT III KKK KKK
MMM MM MMM III KKKKK RRR RRR OOO OOO TTT III KKKKK
MMM MMM III KKK KKK RRRRRR OOO OOO TTT III KKK KKK
MMM MMM III KKK KKK RRR RRR OOOOOO TTT III KKK KKK
MikroTik RouterOS 2.9 (c) 1999-2004 http://www.mikrotik.com/
Terminal xterm detected, using multiline input mode
[admin@MikroTik] >
The command prompt shows the identity name of the router and the current menu level, for example:
[admin@MikroTik] >
[admin@MikroTik] interface>
[admin@MikroTik] ip address>
Commands The list of available commands at any menu level can be obtained by entering the question mark '?', for example:
[admin@MikroTik] >
log/ -- System logs
quit -- Quit console
radius/ -- Radius client settings
certificate/ -- Certificate management
special-login/ -- Special login users
redo -- Redo previously undone action
driver/ -- Driver management
ping -- Send ICMP Echo packets
setup -- Do basic setup of system
interface/ -- Interface configuration
password -- Change password
undo -- Undo previous action
port/ -- Serial ports
import -- Run exported configuration script
snmp/ -- SNMP settings
user/ -- User management
file/ -- Local router file storage.
system/ -- System information and utilities
queue/ -- Bandwidth management
ip/ -- IP options
tool/ -- Diagnostics tools
ppp/ -- Point to Point Protocol
routing/ -- Various routing protocol settings
export --
[admin@MikroTik] >
[admin@MikroTik] ip>
.. -- go up to root
service/ -- IP services
socks/ -- SOCKS version 4 proxy
arp/ -- ARP entries management
upnp/ -- Universal Plug and Play
dns/ -- DNS settings
address/ -- Address management
accounting/ -- Traffic accounting
the-proxy/ --
vrrp/ -- Virtual Router Redundancy Protocol
pool/ -- IP address pools
packing/ -- Packet packing settings
neighbor/ -- Neighbors
route/ -- Route management
firewall/ -- Firewall management
dhcp-client/ -- DHCP client settings
dhcp-relay/ -- DHCP relay settings
dhcp-server/ -- DHCP server settings
hotspot/ -- HotSpot management
ipsec/ -- IP security
web-proxy/ -- HTTP proxy
export --
[admin@MikroTik] ip>
The list of available commands and menus has short descriptions next to the items. You can move to the desired menu level by typing its name and hitting the [Enter] key, for example:
[admin@MikroTik] > | Base level menu
[admin@MikroTik] > driver | Enter 'driver' to move to the driver
| level menu
[admin@MikroTik] driver> / | Enter '/' to move to the base level menu
| from any level
[admin@MikroTik] > interface | Enter 'interface' to move to the
| interface level menu
[admin@MikroTik] interface> /ip | Enter '/ip' to move to the IP level menu
| from any level
[admin@MikroTik] ip> |
A command or an argument does not need to be completed, if it is not ambiguous. For example, instead of typing interface you can type just in or int. To complete a command use the [Tab] key. Note that the completion is optional, and you can just use short command and parameter names
The commands may be invoked from the menu level, where they are located, by typing its name. If the command is in a different menu level than the current one, then the command should be invoked using its full (absolute) or relative path, for example:
[admin@MikroTik] ip route> print | Prints the routing table
[admin@MikroTik] ip route> .. address print | Prints the IP address table
[admin@MikroTik] ip route> /ip address print | Prints the IP address table
The commands may have arguments. The arguments have their names and values. Some commands, may have a required argument that has no name.
Summary on executing the commands and navigating the menus | Command | Action |
| command [Enter] | Executes the command |
| [?] | Shows the list of all available commands |
| command [?] | Displays help on the command and the list of arguments |
| command argument [?] | Displays help on the command's argument |
| [Tab] | Completes the command/word. If the input is ambiguous, a second [Tab] gives possible options |
| / | Moves up to the base level |
| /command | Executes the base level command |
| .. | Moves up one level |
| "" | Specifies an empty string |
| "word1 word2" | Specifies a string of 2 words that contain a space |
You can abbreviate names of levels, commands and arguments.
For the IP address configuration, instead of using the address and netmask arguments, in most cases you can specify the address together with the number of true bits in the network mask, i.e., there is no need to specify the netmask separately. Thus, the following two entries would be equivalent:
/ip address add address 10.0.0.1/24 interface ether1
/ip address add address 10.0.0.1 netmask 255.255.255.0 interface ether1
Notes
You must specify the size of the network mask in the address argument, even if it is the 32-bit subnet, i.e., use 10.0.0.1/32 for address=10.0.0.1 netmask=255.255.255.255
Basic Configuration Tasks
Description
Interface Management Before configuring the IP addresses and routes please check the /interface menu to see the list of available interfaces. If you have Plug-and-Play cards installed in the router, it is most likely that the device drivers have been loaded for them automatically, and the relevant interfaces appear on the /interface print list, for example:
[admin@MikroTik] interface> print
Flags: X - disabled, D - dynamic, R - running
# NAME TYPE RX-RATE TX-RATE MTU
0 R ether1 ether 0 0 1500
1 R ether2 ether 0 0 1500
2 X wavelan1 wavelan 0 0 1500
3 X prism1 wlan 0 0 1500
[admin@MikroTik] interface>
The interfaces need to be enabled, if you want to use them for communications. Use the /interface enable name command to enable the interface with a given name or number, for example:
[admin@MikroTik] interface> print
Flags: X - disabled, D - dynamic, R - running
# NAME TYPE RX-RATE TX-RATE MTU
0 X ether1 ether 0 0 1500
1 X ether2 ether 0 0 1500
[admin@MikroTik] interface> enable 0
[admin@MikroTik] interface> enable ether2
[admin@MikroTik] interface> print
Flags: X - disabled, D - dynamic, R - running
# NAME TYPE RX-RATE TX-RATE MTU
0 R ether1 ether 0 0 1500
1 R ether2 ether 0 0 1500
[admin@MikroTik] interface>
The interface name can be changed to a more descriptive one by using /interface set command:
[admin@MikroTik] interface> set 0 name=Local; set 1 name=Public
[admin@MikroTik] interface> print
Flags: X - disabled, D - dynamic, R - running
# NAME TYPE RX-RATE TX-RATE MTU
0 R Local ether 0 0 1500
1 R Public ether 0 0 1500
[admin@MikroTik] interface>
Notes
The device drivers for NE2000 compatible ISA cards need to be loaded using the add command under the /drivers menu. For example, to load the driver for a card with IO address 0x280 and IRQ 5, it is enough to issue the command:
[admin@MikroTik] driver> add name=ne2k-isa io=0x280
[admin@MikroTik] driver> print
Flags: I - invalid, D - dynamic
# DRIVER IRQ IO MEMORY ISDN-PROTOCOL
0 D RealTek 8139
1 D Intel EtherExpressPro
2 D PCI NE2000
3 ISA NE2000 280
4 Moxa C101 Synchronous C8000
[admin@MikroTik] driver>
There are some other drivers that should be added manually. Please refer to the respective manual sections for the detailed information on how drivers are to be loaded.
Setup Command
Command name:
/setup Description
The initial setup of the router can be done by using the /setup command which offers the following configuration:
- reset all router configuration
- load interface driver
- configure ip address and gateway
- setup dhcp client
- setup dhcp server
- setup pppoe client
- setup pptp client
Configure IP address on router, using the Setup command
Execute the /setup command from command line:
[admin@MikroTik] > setup
Setup uses Safe Mode. It means that all changes that are made during setup
are reverted in case of error, or if [Ctrl]+[C] is used to abort setup. To keep
changes exit setup using the [X] key.
[Safe Mode taken]
Choose options by pressing one of the letters in the left column, before
dash. Pressing [X] will exit current menu, pressing Enter key will select the
entry that is marked by an '*'. You can abort setup at any time by pressing
[Ctrl]+[C].
Entries marked by '+' are already configured.
Entries marked by '-' cannot be used yet.
Entries marked by 'X' cannot be used without installing additional packages.
r - reset all router configuration
+ l - load interface driver
* a - configure ip address and gateway
d - setup dhcp client
s - setup dhcp server
p - setup pppoe client
t - setup pptp client
x - exit menu
your choice [press Enter to configure ip address and gateway]: a
To configure IP address and gateway, press a or [Enter], if the a choice is marked with an asterisk symbol ('*').
* a - add ip address
- g - setup default gateway
x - exit menu
your choice [press Enter to add ip address]: a
Choose a to add an IP address. At first, setup will ask you for an interface to which the address will be assigned. If the setup offers you an undesirable interface, erase this choice, and press the [Tab] key twice to see all available interfaces. After the interface is chosen, assign IP address and network mask on it:
your choice: a
enable interface:
ether1 ether2 wlan1
enable interface: ether1
ip address/netmask: 10.1.0.66/24
#Enabling interface
/interface enable ether1
#Adding IP address
/ip address add address=10.1.0.66/24 interface=ether1 comment="added by setup"
+ a - add ip address
* g - setup default gateway
x - exit menu
your choice: x
Basic Examples
Example
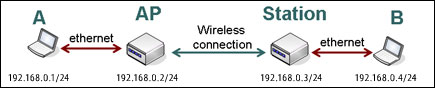
Assume you need to configure the MikroTik router for the following network setup:
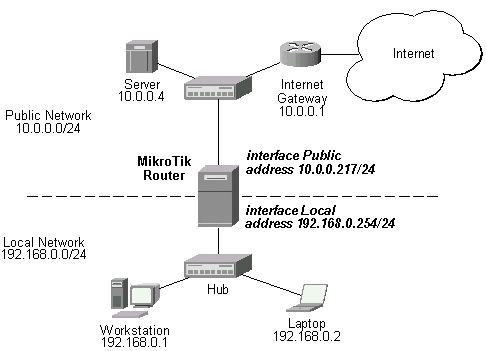
In the current example we use two networks:
- The local LAN with network address 192.168.0.0 and 24-bit netmask: 255.255.255.0. The router's address is 192.168.0.254 in this network
- The ISP's network with address 10.0.0.0 and 24-bit netmask 255.255.255.0. The router's address is 10.0.0.217 in this network
The addresses can be added and viewed using the following commands:
[admin@MikroTik] ip address> add address 10.0.0.217/24 interface Public
[admin@MikroTik] ip address> add address 192.168.0.254/24 interface Local
[admin@MikroTik] ip address> print
Flags: X - disabled, I - invalid, D - dynamic
# ADDRESS NETWORK BROADCAST INTERFACE
0 10.0.0.217/24 10.0.0.217 10.0.0.255 Public
1 192.168.0.254/24 192.168.0.0 192.168.0.255 Local
[admin@MikroTik] ip address>
Here, the network mask has been specified in the value of the address argument. Alternatively, the argument 'netmask' could have been used with the value '255.255.255.0'. The network and broadcast addresses were not specified in the input since they could be calculated automatically.
Please note that the addresses assigned to different interfaces of the router should belong to different networks.
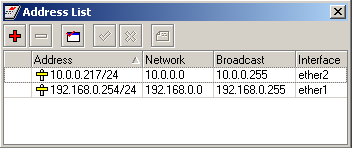
Viewing Routes
You can see two dynamic (D) and connected (C) routes, which have been added automatically when the addresses were added in the example above:
[admin@MikroTik] ip route> print
Flags: A - active, X - disabled, I - invalid, D - dynamic, C - connect,
S - static, r - rip, b - bgp, o - ospf, d - dynamic
# DST-ADDRESS G GATEWAY DISTANCE INTERFACE
0 ADC 192.168.0.0/24 r 0.0.0.0 0 Local
1 ADC 10.0.0.0/24 r 0.0.0.0 0 Public
[admin@MikroTik] ip route> print detail
Flags: A - active, X - disabled, I - invalid, D - dynamic, C - connect,
S - static, r - rip, b - bgp, o - ospf, d - dynamic
0 ADC dst-address=192.168.0.0/24 prefsrc=192.168.0.254 interface=Local scope=10
1 ADC dst-address=10.0.0.0/24 prefsrc=10.0.0.217 interface=Public scope=10
[admin@MikroTik] ip route>
These routes show, that IP packets with destination to 10.0.0.0/24 would be sent through the interface Public, whereas IP packets with destination to 192.168.0.0/24 would be sent through the interface Local. However, you need to specify where the router should forward packets, which have destination other than networks connected directly to the router.
Adding Default Routes
In the following example the default route (destination 0.0.0.0 (any), netmask 0.0.0.0 (any)) will be added. In this case it is the ISP's gateway 10.0.0.1, which can be reached through the interface Public
[admin@MikroTik] ip route> add gateway=10.0.0.1
[admin@MikroTik] ip route> print
Flags: X - disabled, I - invalid, D - dynamic, J - rejected,
C - connect, S - static, R - rip, O - ospf, B - bgp
# DST-ADDRESS G GATEWAY DISTANCE INTERFACE
0 ADC 192.168.0.0/24 Local
1 ADC 10.0.0.0/24 Public
2 A S 0.0.0.0/0 r 10.0.0.1 0 Public
[admin@MikroTik] ip route>
Here, the default route is listed under #2. As we see, the gateway 10.0.0.1 can be reached through the interface 'Public'. If the gateway was specified incorrectly, the value for the argument 'interface' would be unknown.
Notes
You cannot add two routes to the same destination, i.e., destination-address/netmask! It applies to the default routes as well. Instead, you can enter multiple gateways for one destination. For more information on IP routes, please read the Routes, Equal Cost Multipath Routing, Policy Routing manual.
If you have added an unwanted static route accidentally, use the remove command to delete the unneeded one. You will not be able to delete dynamic (DC) routes. They are added automatically and represent routes to the networks the router connected directly.
Testing the Network Connectivity
From now on, the /ping command can be used to test the network connectivity on both interfaces. You can reach any host on both connected networks from the router.
How the /ping command works:
[admin@MikroTik] ip route> /ping 10.0.0.4
10.0.0.4 64 byte ping: ttl=255 time=7 ms
10.0.0.4 64 byte ping: ttl=255 time=5 ms
10.0.0.4 64 byte ping: ttl=255 time=5 ms
3 packets transmitted, 3 packets received, 0% packet loss
round-trip min/avg/max = 5/5.6/7 ms
[admin@MikroTik] ip route>
[admin@MikroTik] ip route> /ping 192.168.0.1
192.168.0.1 64 byte ping: ttl=255 time=1 ms
192.168.0.1 64 byte ping: ttl=255 time=1 ms
192.168.0.1 64 byte ping: ttl=255 time=1 ms
3 packets transmitted, 3 packets received, 0% packet loss
round-trip min/avg/max = 1/1.0/1 ms
[admin@MikroTik] ip route>
The workstation and the laptop can reach (ping) the router at its local address 192.168.0.254, If the router's address 192.168.0.254 is specified as the default gateway in the TCP/IP configuration of both the workstation and the laptop, then you should be able to ping the router:
C:\>ping 192.168.0.254
Reply from 192.168.0.254: bytes=32 time=10ms TTL=253
Reply from 192.168.0.254: bytes=32 time<10ms TTL=253
Reply from 192.168.0.254: bytes=32 time<10ms TTL=253
C:\>ping 10.0.0.217
Reply from 10.0.0.217: bytes=32 time=10ms TTL=253
Reply from 10.0.0.217: bytes=32 time<10ms TTL=253
Reply from 10.0.0.217: bytes=32 time<10ms TTL=253
C:\>ping 10.0.0.4
Request timed out.
Request timed out.
Request timed out.
Notes
You cannot access anything beyond the router (network 10.0.0.0/24 and the Internet), unless you do the one of the following:
- Use source network address translation (masquerading) on the MikroTik router to 'hide' your private LAN 192.168.0.0/24 (see the information below), or
- Add a static route on the ISP's gateway 10.0.0.1, which specifies the host 10.0.0.217 as the gateway to network 192.168.0.0/24. Then all hosts on the ISP's network, including the server, will be able to communicate with the hosts on the LAN
To set up routing, it is required that you have some knowledge of configuring TCP/IP networks. We strongly recommend that you obtain more knowledge, if you have difficulties configuring your network setups.
Advanced Configuration Tasks
Description
Next will be discussed situation with 'hiding' the private LAN 192.168.0.0/24 'behind' one address 10.0.0.217 given to you by the ISP.
Application Example with Masquerading
If you want to 'hide' the private LAN 192.168.0.0/24 'behind' one address 10.0.0.217 given to you by the ISP, you should use the source network address translation (masquerading) feature of the MikroTik router. Masquerading is useful, if you want to access the ISP's network and the Internet appearing as all requests coming from the host 10.0.0.217 of the ISP's network. The masquerading will change the source IP address and port of the packets originated from the network 192.168.0.0/24 to the address 10.0.0.217 of the router when the packet is routed through it.
Masquerading conserves the number of global IP addresses required and it lets the whole network use a single IP address in its communication with the world.
To use masquerading, a source NAT rule with action 'masquerade' should be added to the firewall configuration:
[admin@MikroTik] ip firewall nat> add chain=srcnat action=masquerade out-interface=Public
[admin@MikroTik] ip firewall nat> print
Flags: X - disabled, I - invalid, D - dynamic
0 chain=srcnat out-interface=Public action=masquerade
Notes
Please consult Network Address Translation for more information on masquerading.
Example with Bandwidth Management
Assume you want to limit the bandwidth to 128kbps on downloads and 64kbps on uploads for all hosts on the LAN. Bandwidth limitation is done by applying queues for outgoing interfaces regarding the traffic flow. It is enough to add a single queue at the MikroTik router:
[admin@MikroTik] queue simple> add max-limit=64000/128000 interface=Local
[admin@MikroTik] queue simple> print
Flags: X - disabled, I - invalid, D - dynamic
0 name="queue1" target-address=0.0.0.0/0 dst-address=0.0.0.0/0
interface=Local queue=default/default priority=8 limit-at=0/0
max-limit=64000/128000 total-queue=default
[admin@MikroTik] queue simple>
Leave all other parameters as set by default. The limit is approximately 128kbps going to the LAN (download) and 64kbps leaving the client's LAN (upload).
Example with NAT
Assume we have moved the server in our previous examples from the public network to our local one:
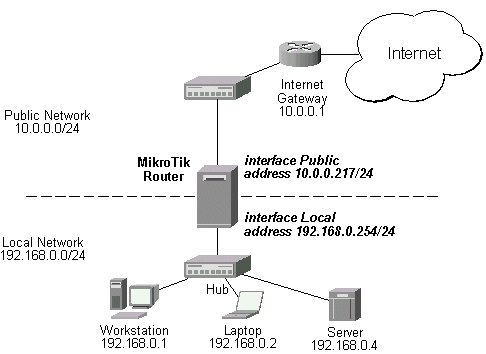
The server's address is now 192.168.0.4, and we are running web server on it that listens to the TCP port 80. We want to make it accessible from the Internet at address:port 10.0.0.217:80. This can be done by means of Static Network Address translation (NAT) at the MikroTik Router. The Public address:port 10.0.0.217:80 will be translated to the Local address:port 192.168.0.4:80. One destination NAT rule is required for translating the destination address and port:
[admin@MikroTik] ip firewall nat> add chain=dstnat action=dst-nat protocol=tcp dst-address=10.0.0.217/32
dst-port=80 to-addresses=192.168.0.4
[admin@MikroTik] ip firewall nat> pr
Flags: X - disabled, I - invalid, D - dynamic
0 chain=dstnat dst-address=10.0.0.217/32 protocol=tcp dst-port=80
action=dst-nat to-addresses=192.168.0.4 to-ports=0-65535
Notes
Please consult Network Address Translation for more information on Network Address Translation.
source : http://www.mikrotik.com/testdocs/ros/2.9/guide/basic.php